- Nov 7, 2025
Staying Ahead of Social Engineering Attacks
- Andy Scott
- Cyber Security
- 0 comments
Through 2025, in the UK we’ve all seen headlines about major data compromises across industries especially retail. While the technology behind these breaches can seem complex, one common thread runs through many of them: social engineering. Instead of hacking through firewalls, attackers are increasingly going after the easiest and most effective entry point - people.
What Is Social Engineering?
Social engineering is the practice of manipulating individuals into revealing information or performing actions that compromise security. Think of it as a con artist’s toolkit, applied in the digital world. Examples include:
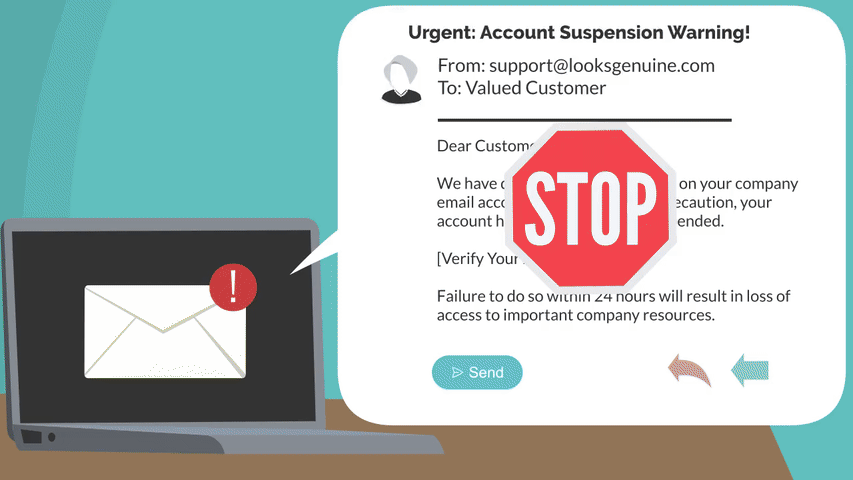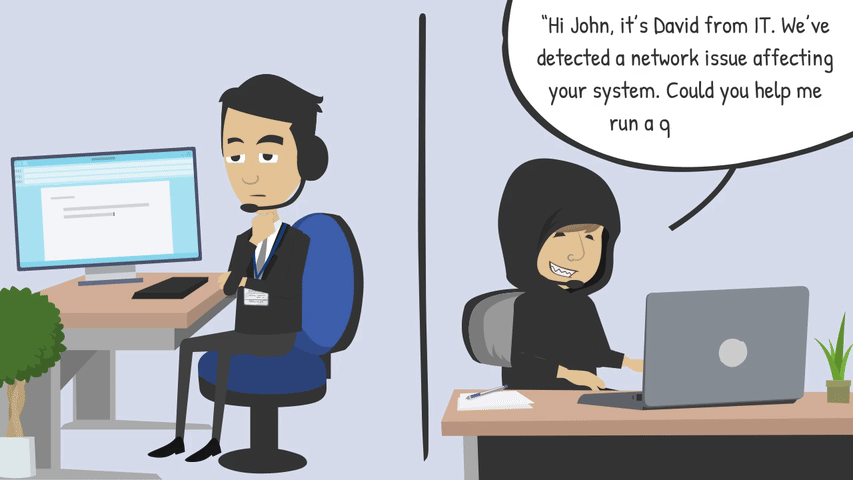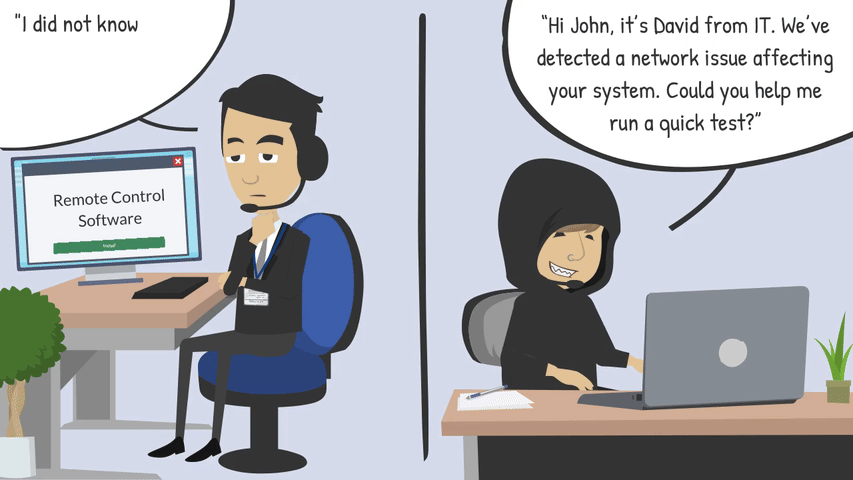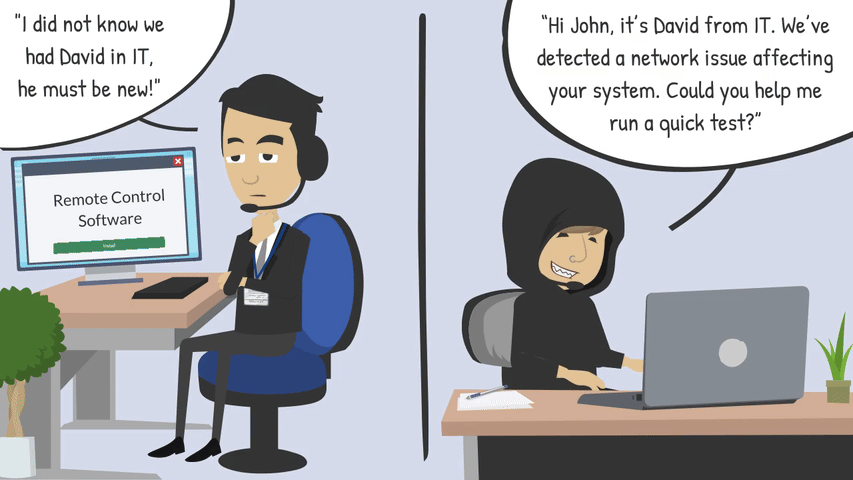
Phishing emails that trick you into clicking malicious links or sharing login details.
Phone calls or text messages posing as IT support, vendors, or even leadership.
Impersonation on collaboration platforms or social media.
Humans are the weakest link: The aim is always the same: exploit human trust to bypass our technical defences.
Why Social Engineering Is So Dangerous
Unlike malware or system exploits, social engineering doesn’t rely on flaws in software - it relies on us letting our guard down. Even the most security savvy organisations can be put at risk if just one employee is deceived. Attackers know this and will patiently research, tailor, and time their approach for maximum success.
Recent incidents across industries have shown that a well designed phishing campaign or impersonation attempt can lead to:
Unauthorised access to sensitive company data.
Theft of intellectual property or trade secrets.
Financial fraud or fraudulent payments.
Significant reputational damage.
How Employees Can Stay Vigilant
Security isn’t just the responsibility of IT and security teams - it’s part of everyone’s daily work. Here are some practical ways to protect yourself:
Pause before you click. If an email or link seems unexpected, doublecheck before engaging.
Verify requests through trusted channels. If you receive an urgent message asking for credentials, payments, or sensitive information, confirm it by phone or in-person with the requester.
Watch for red flags. Spelling errors, unusual tone, or odd formatting are common in phishing attempts.
Guard your credentials. Never share passwords, multifactor authentication codes, or system access with anyone. No one legitimate will ever ask for them.
Report suspicious activity. Forward questionable emails or incidents to your IT or Security team immediately - it’s better to be cautious than to assume.
Be cautious about oversharing. Details about projects, planned absences, or team structures posted publicly can help attackers craft convincing scams.
Our Collective Responsibility
Technology will continue to evolve, and so will the tactics of cybercriminals. The strongest defence we have is a culture of vigilance, where every employee treats unexpected digital interactions with healthy scepticism.
Remember: staying secure is not about paranoia - it’s about awareness. Each of us plays a role in protecting ourselves, our friends, our colleagues, and our customers from becoming the next headline.